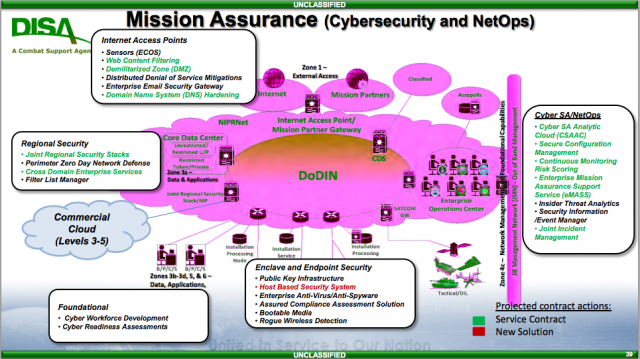
The Fraying Edge: Limits Of The Army’s Global Network
Posted on
The Army wants a single seamless data system from home base to the front line. That’s even harder than it sounds.
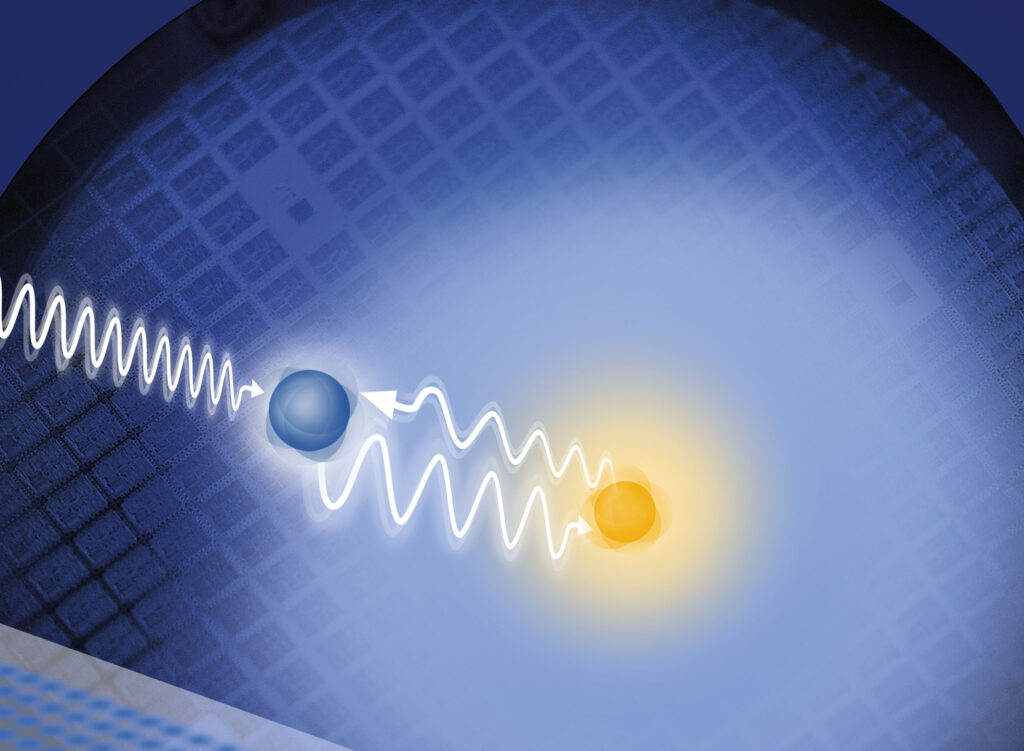
‘Golden Age Of SIGINT May Be Over’: New Encryption Foils IC Eavesdropping
Posted on
“End-to-end encryption of all communications and data, differential privacy, and secure communications for all users are likely to be the new reality,” says a new DARPA-funded study.
DoD Awards Contract To Break Its Security Clearance Logjam
Posted on
Can artificial intelligence, machine learning, and agile development help clear the massive backlog?
How To Wage Global Cyber War: Nakasone, Norton, & Deasy
Posted on
The military needs a globe-spanning network to counter threats that no single theater command can cope with. That takes more than just technology.
Common Cyber Standards Will Steamroller Hold-Outs: DoD Officials
Posted on
This year promises to be a year of big changes in how the Defense Department does Cyber — and leaders are warning staffers that it’s not going to be business as usual.
Pentagon Builds Mega-Database For Spectrum & Electronic Warfare
Posted on
The JSDR database won’t just keep American communications officers from mistakenly scrambling each others’ signals, either. By providing a comprehensive baseline of what friendly transmissions look like, the mega-database will make it easier for Signals Intelligence (SIGINT) and Electronic Warfare (EW) troops to hone in on enemy transmissions.
Bad Cybersecurity? No Access To DoD Networks
Posted on
“We’re going to turn that off unless you secured that properly. Whoa! That’s a very different mindset,” Col. Straub told me. “The availability of the network versus the defense of the network, that’s something we’re trying to get commanders to think about.”
Whack 7 DoD Agencies, HASC Chair’s Bill Proposes
Posted on
Pentagon brass are taking a look at what chaff can be cut in order to push along weapons systems like lasers and hypersonics. And they have some powerful Capitol Hill allies.
Open Architecture: The Devils ARE In The Details
Posted on
WASHINGTON: Two years ago, Capt. John Zimmerman and his award-winning Navy team were testing a software upgrade for submarines when they ran into a surprising problem. When they changed the code controlling the Tomahawk missile launchers, the torpedo tubes stopped working. Fortunately, this all happened in a laboratory ashore before the upgrade got anywhere near the… Keep reading →
Who Commands In Cyberspace As New HQ Expands?
Posted on
TYSON’S CORNER: “Unity of command” is a classic principle of war. As the US military struggles to improve cybersecurity against relentless Russian, Chinese, and other attacks, however, it’s finding the complex interconnectedness of computer networks complicate the chain of command. If the tech guys urgently need to shut a system down — say, because it’s… Keep reading →